在 Ubuntu 15.04 中如何安装和使用 Snort
| 2015-09-03 09:07:00 评论: 2
对于网络安全而言入侵检测是一件非常重要的事。入侵检测系统(IDS)用于检测网络中非法与恶意的请求。Snort是一款知名的开源的入侵检测系统。其 Web界面(Snorby)可以用于更好地分析警告。Snort使用iptables/pf防火墙来作为入侵检测系统。本篇中,我们会安装并配置一个开源的入侵检测系统snort。

Snort 安装
要求
snort所使用的数据采集库(DAQ)用于一个调用包捕获库的抽象层。这个在snort上就有。下载过程如下截图所示。
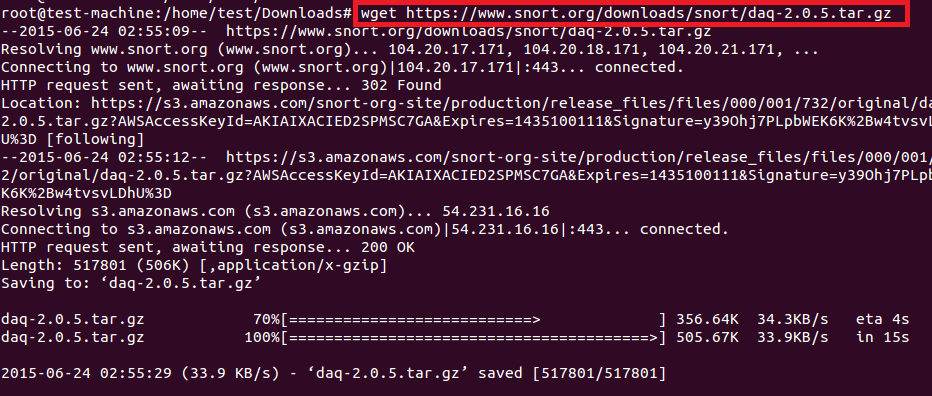
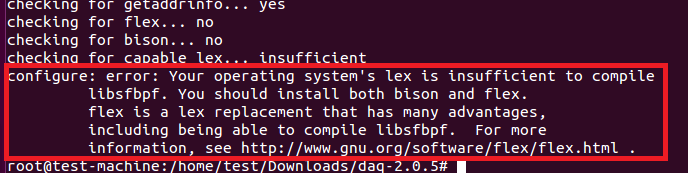
解压并运行./configure、make、make install来安装DAQ。然而,DAQ要求其他的工具,因此,./configure脚本会生成下面的错误。
flex和bison错误
libpcap错误
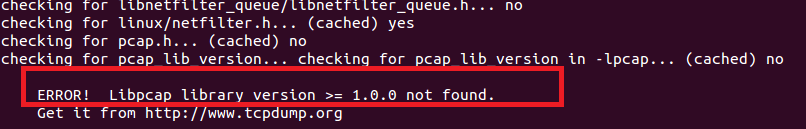
因此在安装DAQ之前先安装flex/bison和libcap。
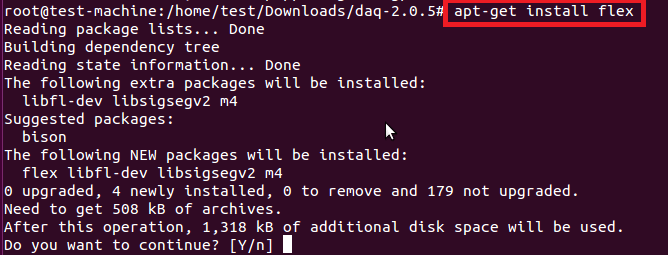
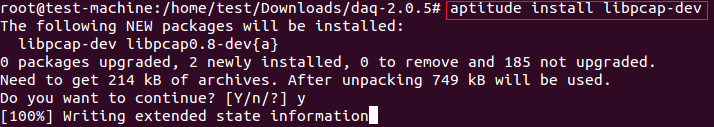
如下所示安装libpcap开发库
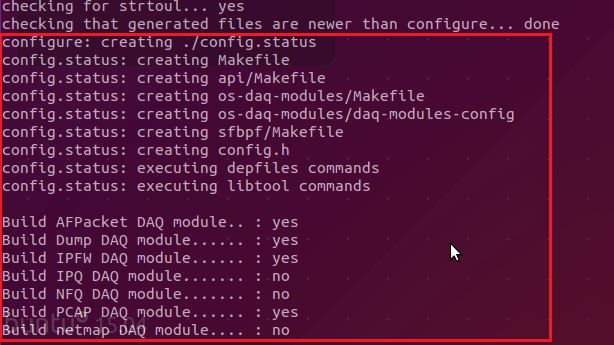
安装完必要的工具后,再次运行./configure脚本,将会显示下面的输出。
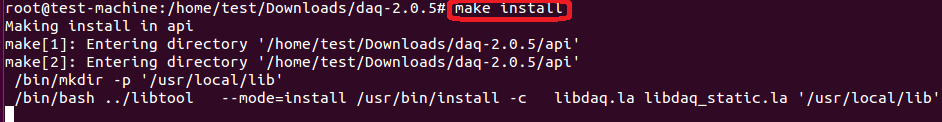
make和make install 命令的结果如下所示。
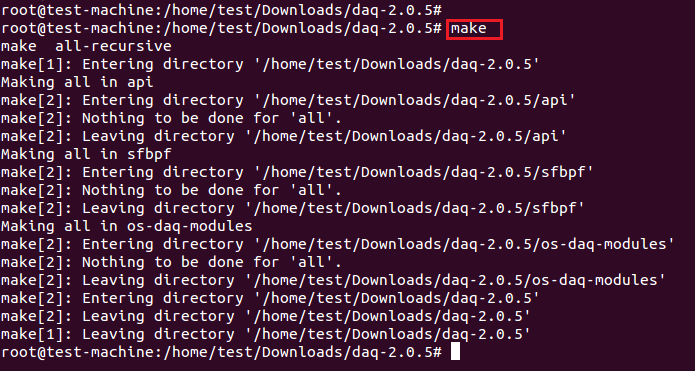
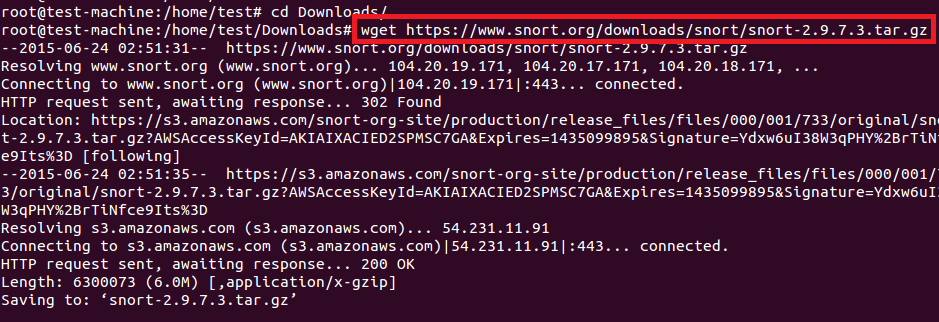
成功安装DAQ之后,我们现在安装snort。如下图使用wget下载它。
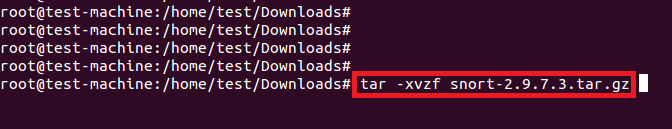
使用下面的命令解压安装包。
#tar -xvzf snort-2.9.7.3.tar.gz
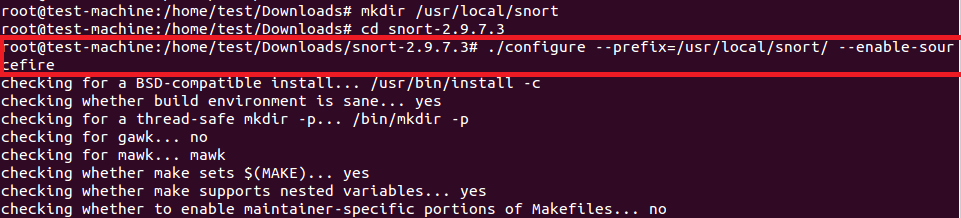
创建安装目录并在脚本中设置prefix参数。同样也建议启用包性能监控(PPM)的sourcefire标志。
#mkdir /usr/local/snort
#./configure --prefix=/usr/local/snort/ --enable-sourcefire
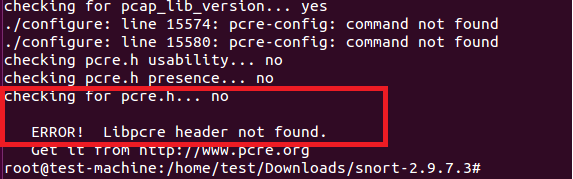
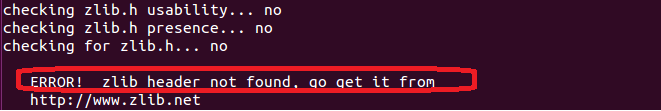
配置脚本会由于缺少libpcre-dev、libdumbnet-dev 和zlib开发库而报错。
配置脚本由于缺少libpcre库报错。
配置脚本由于缺少dnet(libdumbnet)库而报错。
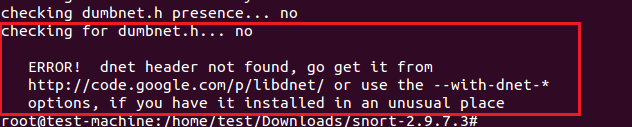
配置脚本由于缺少zlib库而报错
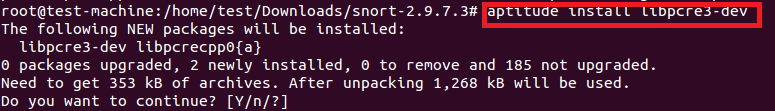
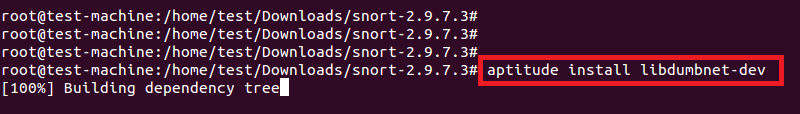
如下所示,安装所有需要的开发库。
# aptitude install libpcre3-dev
# aptitude install libdumbnet-dev
# aptitude install zlib1g-dev
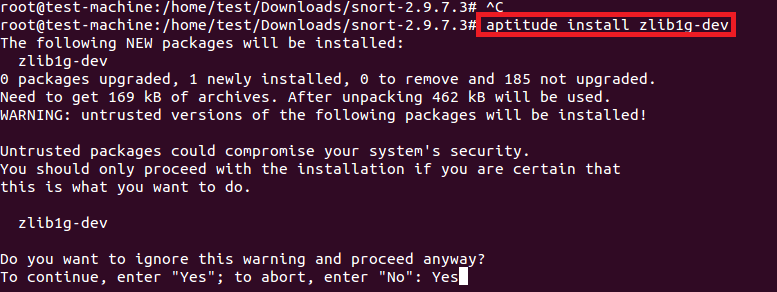
安装完snort需要的库之后,再次运行配置脚本就不会报错了。
运行make和make install命令在/usr/local/snort目录下完成安装。
# make
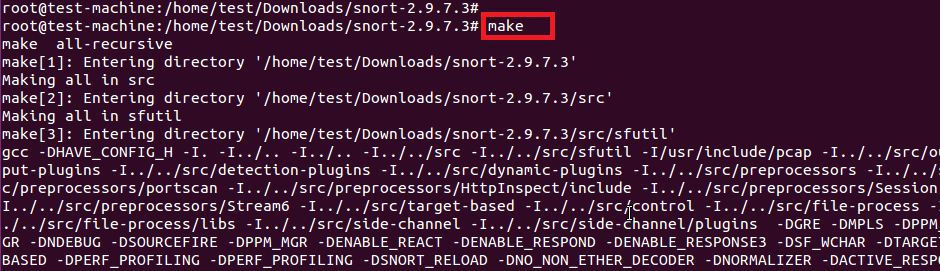
# make install
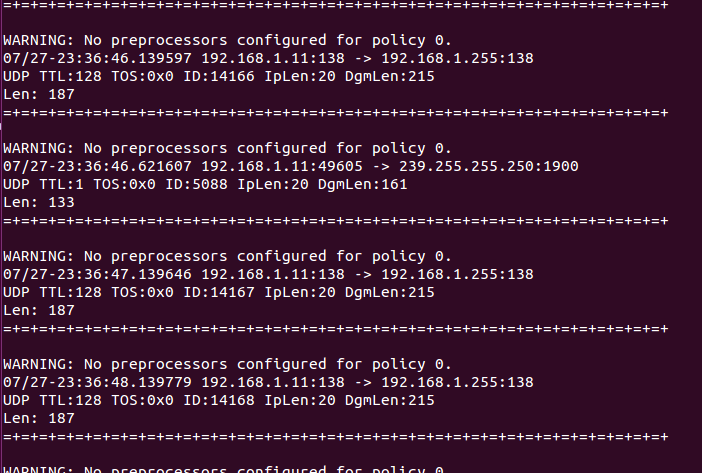
最后,从/usr/local/snort/bin中运行snort。现在它对eth0的所有流量都处在promisc模式(包转储模式)。
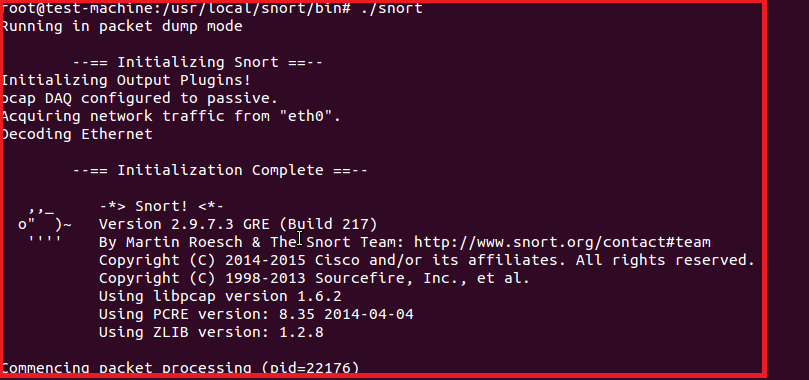
如下图所示snort转储流量。
Snort的规则和配置
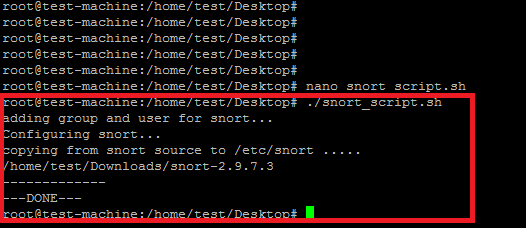
从源码安装的snort还需要设置规则和配置,因此我们需要复制规则和配置到/etc/snort下面。我们已经创建了单独的bash脚本来用于设置规则和配置。它会设置下面这些snort设置。
- 在linux中创建用于snort IDS服务的snort用户。
- 在/etc下面创建snort的配置文件和文件夹。
- 权限设置并从源代码的etc目录中复制数据。
- 从snort文件中移除规则中的#(注释符号)。
#!/bin/bash#
# snort源代码的路径
snort_src="/home/test/Downloads/snort-2.9.7.3"
echo "adding group and user for snort..."
groupadd snort &> /dev/null
useradd snort -r -s /sbin/nologin -d /var/log/snort -c snort_idps -g snort &> /dev/null#snort configuration
echo "Configuring snort..."mkdir -p /etc/snort
mkdir -p /etc/snort/rules
touch /etc/snort/rules/black_list.rules
touch /etc/snort/rules/white_list.rules
touch /etc/snort/rules/local.rules
mkdir /etc/snort/preproc_rules
mkdir /var/log/snort
mkdir -p /usr/local/lib/snort_dynamicrules
chmod -R 775 /etc/snort
chmod -R 775 /var/log/snort
chmod -R 775 /usr/local/lib/snort_dynamicrules
chown -R snort:snort /etc/snort
chown -R snort:snort /var/log/snort
chown -R snort:snort /usr/local/lib/snort_dynamicrules
###copy configuration and rules from etc directory under source code of snort
echo "copying from snort source to /etc/snort ....."
echo $snort_src
echo "-------------"
cp $snort_src/etc/*.conf* /etc/snort
cp $snort_src/etc/*.map /etc/snort##enable rules
sed -i 's/include \$RULE\_PATH/#include \$RULE\_PATH/' /etc/snort/snort.conf
echo "---DONE---"
改变脚本中的snort源目录路径并运行。下面是成功的输出。
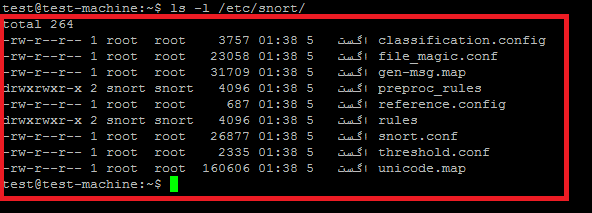
上面的脚本从snort源中复制下面的文件和文件夹到/etc/snort配置文件中
snort的配置非常复杂,要让IDS能正常工作需要进行下面必要的修改。
ipvar HOME_NET 192.168.1.0/24 # LAN side

- mefirst_love [Firefox 47.0|Windows 10] 2016-08-04 10:50
- 你好,我在redhat 6.5 32 位上搭建snort系统,
运行 snort -T -c /etc/snort/snort.conf 命令后,能出现
[ Number of patterns truncated to 20 bytes: 1428 ]
--== Initialization Complete ==--
,,_ -*> Snort! <*-
o" )~ Version 2.9.8.3 GRE (Build 383)
'''' By Martin Roesch & The Snort Team: http://www.snort.org/contact#team
Copyright (C) 2014-2015 Cisco and/or its affiliates. All rights reserved.
Copyright (C) 1998-2013 Sourcefire, Inc., et al.
Using libpcap version 1.4.0
Using PCRE version: 7.8 2008-09-05
Using ZLIB version: 1.2.3
Rules Engine: SF_SNORT_DETECTION_ENGINE Version 2.6 <Build 1>
Preprocessor Object: SF_REPUTATION Version 1.1 <Build 1>
Preprocessor Object: SF_POP Version 1.0 <Build 1>
Preprocessor Object: SF_IMAP Version 1.0 <Build 1>
Preprocessor Object: SF_GTP Version 1.1 <Build 1>
Preprocessor Object: SF_SDF Version 1.1 <Build 1>
Preprocessor Object: SF_DNP3 Version 1.1 <Build 1>
Preprocessor Object: SF_FTPTELNET Version 1.2 <Build 13>
Preprocessor Object: SF_DNS Version 1.1 <Build 4>
Preprocessor Object: SF_SIP Version 1.1 <Build 1>
Preprocessor Object: SF_MODBUS Version 1.1 <Build 1>
Preprocessor Object: SF_DCERPC2 Version 1.0 <Build 3>
Preprocessor Object: SF_SSH Version 1.1 <Build 3>
Preprocessor Object: SF_SMTP Version 1.1 <Build 9>
Preprocessor Object: SF_SSLPP Version 1.1 <Build 4>
Snort successfully validated the configuration!
Snort exiting
但是我在网页上http://localhost/acid/acid_db_setup.php 按照网上的资料,应该能出现各种网络流量图,结果出现如下的错误,能帮忙指点下看问题出在哪里了没?
Strict Standards: Declaration of MultipleElementCriteria::SanitizeElement() should be compatible with BaseCriteria::SanitizeElement() in /usr/local/apache/htdocs/acid/acid_state_citems.inc on line 283
Strict Standards: Declaration of MultipleElementCriteria::PrintForm() should be compatible with BaseCriteria::PrintForm() in /usr/local/apache/htdocs/acid/acid_state_citems.inc on line 283
Strict Standards: Declaration of MultipleElementCriteria::AddFormItem() should be compatible with BaseCriteria::AddFormItem() in /usr/local/apache/htdocs/acid/acid_state_citems.inc on line 283
Strict Standards: Declaration of MultipleElementCriteria::SetFormItemCnt() should be compatible with BaseCriteria::SetFormItemCnt() in /usr/local/apache/htdocs/acid/acid_state_citems.inc on line 283
Strict Standards: Declaration of ProtocolFieldCriteria::Description() should be compatible with BaseCriteria::Description() in /usr/local/apache/htdocs/acid/acid_state_citems.inc on line 311
Fatal error: Call-time pass-by-reference has been removed in /usr/local/apache/htdocs/acid/acid_state_citems.inc on line 325
补充说明下,php,mysql 等需要的环境都配置测试正常,
- CC-顺爷 [Chrome 31.0|Windows 7] 2016-04-10 19:41
- '''